PASS DECRYPTOR : Hacking an Instagram account: Protection methods
PASS DECRYPTOR: in summary
PASS DECRYPTOR is the application designed to unlock an Instagram profile, including private accounts, within minutes.
By providing the username (@handle), a phone number, or an email address, PASS DECRYPTOR extracts the password associated with the account.
You can learn more about PASS DECRYPTOR directly from its official website: https://www.passwordrevelator.net/fr/passdecryptor
How can hackers compromise an Instagram account?
Why do hackers target Instagram?
Instagram, an image-sharing platform with over 1.3 billion monthly active users, is a prime target for hackers seeking to compromise accounts. This massive popularity makes it fertile ground for intrusion attempts aimed at accessing users' personal data.
Social media platforms exhibit various security vulnerabilities that crackers exploit daily to hack passwords. Account breaches are constantly increasing and affect all types of users.
Reasons behind hacking attempts:
- Carry out malicious pranks
- Hack the Instagram account of a professional rival
- Fraudulently impersonate someone else
- Monitor a partner's activities
Often, hackers exploit compromised accounts to send spam messages to the victim's contacts. The main danger lies in unauthorized access to confidential information once they have successfully cracked the Instagram password.
Six methods used to hack an Instagram account
Here is an overview of the main strategies hackers use to compromise and crack Instagram accounts.
Method 1: Automated data collection (Web Scraping)
This approach involves mass-gathering information available online. Databases containing login credentials sometimes circulate freely on certain websites. Using automated programs, hackers collect and sort this information to identify vulnerable accounts they can compromise.
Method 2: Phishing pages
This is a widely used technique where the hacker creates a perfect replica of the Instagram login page to steal credentials. Typically, the victim receives a deceptive message such as: "Someone viewed your profile—click here to see who." The link leads to the fake login page.
When the user enters their password, it is instantly sent to the hacker. The page then redirects to the real Instagram site, leaving the victim unaware that their account has just been compromised.
Method 3: Bypassing two-factor authentication (SIM Swapping)
Two-factor authentication adds a security layer by sending a code via SMS. However, this protection can be bypassed by crackers using the "SIM Swapping" technique to hack the account. The hacker contacts the mobile carrier, impersonating the legitimate account holder and claiming a lost or malfunctioning SIM card.
They then request the phone number to be transferred to a new SIM card under their control. Once this manipulation is complete, the attacker directly receives verification codes and can easily compromise the Instagram account.
Method 4: Remote Access Tools (RATs)
RATs (Remote Access Tools) allow a hacker to take remote control of a computer to steal information. With these hacking tools, they can monitor screen activity, track browsing behavior, and even install keyloggers (keystroke recorders).
These keyloggers capture every keystroke, creating a complete log of everything typed—including Instagram passwords. The attacker can also copy files from the hard drive without the victim noticing, enabling them to compromise not only Instagram but other accounts as well.
Method 5: Trojan horses
Trojans are among the most widespread hacking tools used by cybercriminals today. They primarily spread through warez sites offering illegal free content. When a user downloads movies, software, or other content from these dubious sources, cracks or key generators often contain malware.
The user gets the desired content, but their device is simultaneously infected with malicious software that attackers use to steal personal information and crack their Instagram password.
Method 6: Infected keygens (Key generators)
Running patches or keygens downloaded from untrusted sources often silently installs spyware. These hacking programs—such as the infamous Trojan Turkojan, which compromised hundreds of thousands of computers worldwide—give attackers extensive capabilities to crack and steal Instagram credentials.
Security recommendations against hacking
The methods described above represent only a sample of the techniques hackers use to compromise Instagram accounts. Numerous other approaches are regularly employed by attackers to crack passwords.
For example, on a shared local network, a hacker can intercept data transmitted by other computers connected to the same router and thereby steal your credentials. This is why it is strongly recommended to always enable secure connections (HTTPS) whenever available to prevent being hacked.
Protection tips against hacking:
- Use unique and complex passwords that are hard to crack
- Enable two-factor authentication to make hacking more difficult
- Always verify the URL of login pages to avoid phishing
- Avoid clicking on suspicious links used by hackers
- Never download cracks, keygens, or software from unofficial sources
- Keep your devices and applications updated to prevent security vulnerabilities
- Beware of public Wi-Fi networks where hackers can intercept your data
- Regularly change your Instagram password to reduce hacking risks
Its benefits
power consumption
energy saver
ISO 9001
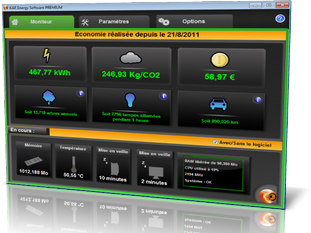
 PASS DECRYPTOR - Data setting
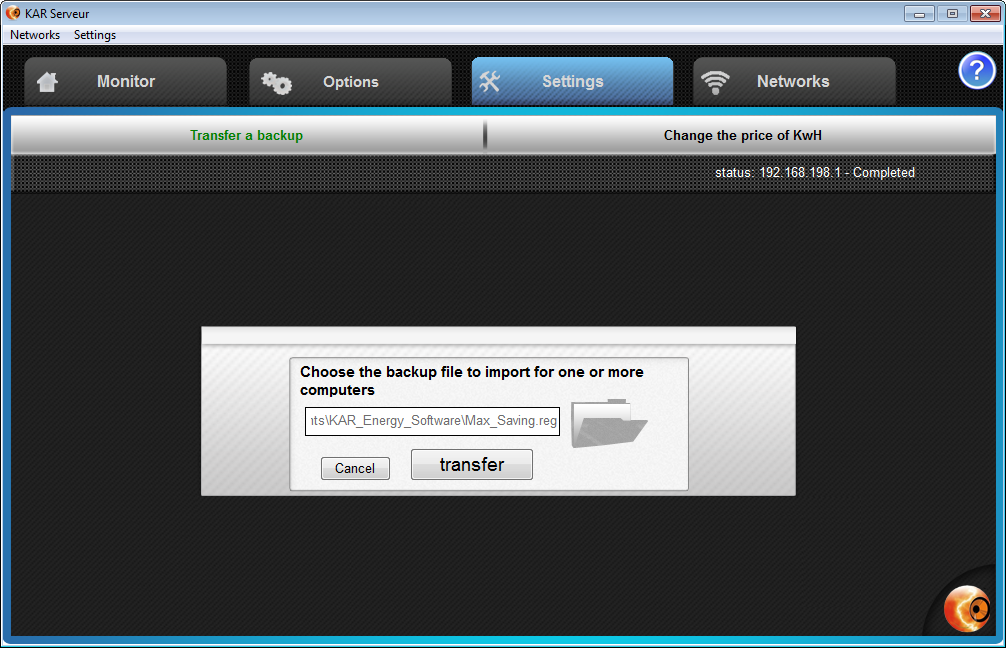
PASS DECRYPTOR - Data setting 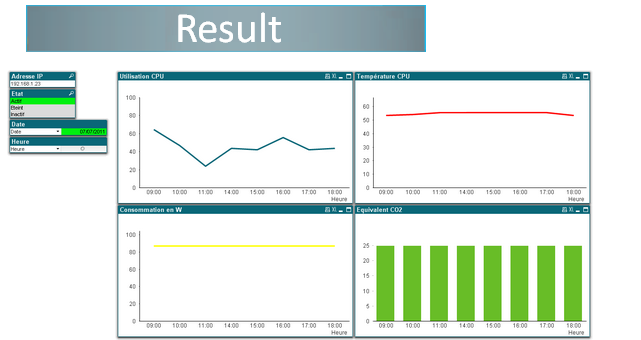 PASS DECRYPTOR - Graphic
PASS DECRYPTOR - Graphic 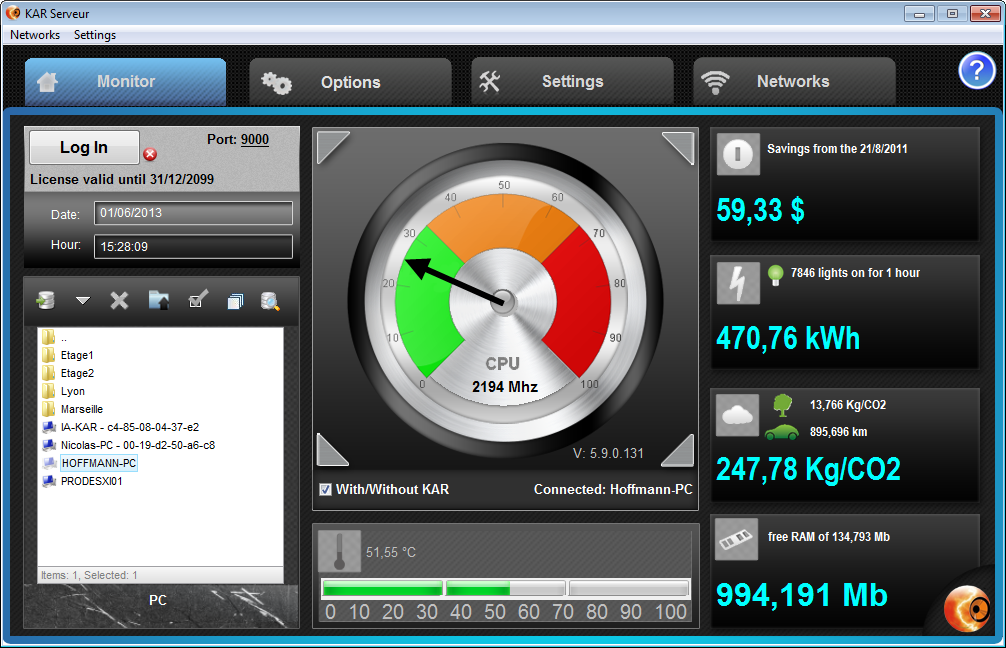 PASS DECRYPTOR - Data management
PASS DECRYPTOR - Data management 


PASS DECRYPTOR: its rates
standard
Rate
On demand
Clients alternatives to PASS DECRYPTOR

Comprehensive energy tracking, real-time analytics, predictive insights, and customizable reporting tools enhance energy management efficiency.
See more details See less details
Kelvin offers a robust suite of features designed for effective energy management. Users benefit from comprehensive energy tracking that helps monitor consumption patterns. Real-time analytics provide instant insights into usage, allowing for timely adjustments. Predictive insights aid in forecasting future energy needs, while customizable reporting tools enable tailored evaluations of performance. Together, these functionalities empower organizations to optimize their energy utilization and reduce costs.
Read our analysis about kelvin
Streamline your energy management with powerful software that tracks usage, costs, and emissions in real-time.
See more details See less details
Goby's energy management software provides a comprehensive view of your energy consumption, identifies savings opportunities, and helps you meet sustainability goals. With automated data collection and analysis, you can easily make informed decisions to optimize energy usage and reduce costs.
Read our analysis about Goby
Streamline inspections with easy-to-use software. Ensure compliance, identify trends, and take corrective action.
See more details See less details
iAuditor allows you to create custom checklists, schedule inspections, and assign tasks to team members. Its powerful analytics feature provides real-time insights to help you make data-driven decisions and improve overall performance. Save time and reduce risk with iAuditor.
Read our analysis about SafetyCulture Appvizer Community Reviews (0) The reviews left on Appvizer are verified by our team to ensure the authenticity of their submitters.
Write a review No reviews, be the first to submit yours.
