Software • September 9, 2025
The 15 best IT asset management software packages for controlled asset management
Discover our complete guide and our top 15 software to choose the ideal ITAM software and optimize your IT asset management.

Software Alternative to Microsoft Copilot: 9 AI programs for greater efficiency 9 alternatives to Copilot (Microsoft): generalist AIs or industry-specific tools, find the pro assistant best suited to your needs.

Software Freshdesk vs Freshservice: customer support or IT service, which should you choose? Compare Freshdesk and Freshservice: customer support, ITSM, pricing, interface, integrations. Which one will meet your needs in 2025?

Software Top 13 ITSM tools that breathe new life into IT service management Discover our comprehensive comparison of the 13 best ITSM tools and their key features for agile, high-performance IT management.

Software • September 9, 2025
The 15 best IT asset management software packages for controlled asset management
Discover our complete guide and our top 15 software to choose the ideal ITAM software and optimize your IT asset management.

Software • August 28, 2025
Freshservice or ServiceNow: which ITSM solution really wins in 2025?
Compare ServiceNow and Freshservice: features, pricing, integrations and use cases. The complete ITSM guide to making the right choice.

Software • August 19, 2025
Microsoft Copilot vs ChatGPT: which AI is more effective for your productivity?
Copilot or ChatGPT? Compare their features, prices, integrations and use cases to choose the AI best suited to your business in 2025.

Definition • August 13, 2025
Work smarter and more efficiently? AI automation makes it possible!
AI is becoming more and more integrated into our daily business activities, as it increases the efficiency of companies. Discover its many benefits, as well as examples of practical cases and tools.

Software • August 13, 2025
Mistral AI vs ChatGPT: the duel of artificial intelligences in 2025
Mistral AI or ChatGPT? Discover our 2025 comparison: features, price, interface, integrations and reviews to choose the best AI.

Software • August 13, 2025
Mistral AI vs ChatGPT: the duel of artificial intelligences in 2025
Mistral AI or ChatGPT? Discover our 2025 comparison: features, price, interface, integrations and reviews to choose the best AI.

Alternative to Microsoft Copilot: 9 AI programs for greater efficiency 9 alternatives to Copilot (Microsoft): generalist AIs or industry-specific tools, find the pro assistant best suited to your needs.

Freshdesk vs Freshservice: customer support or IT service, which should you choose? Compare Freshdesk and Freshservice: customer support, ITSM, pricing, interface, integrations. Which one will meet your needs in 2025?

Top 13 ITSM tools that breathe new life into IT service management Discover our comprehensive comparison of the 13 best ITSM tools and their key features for agile, high-performance IT management.

The 15 best IT asset management software packages for controlled asset management Discover our complete guide and our top 15 software to choose the ideal ITAM software and optimize your IT asset management.

Atera
RMM
IT Management
Managed Service Providers (MSP)
Professional Services Automation (PSA)
Patch Management
SuperOps RMM
RMM
Learn more about SuperOps RMM
QuickBase
Application Development
Learn more about QuickBase
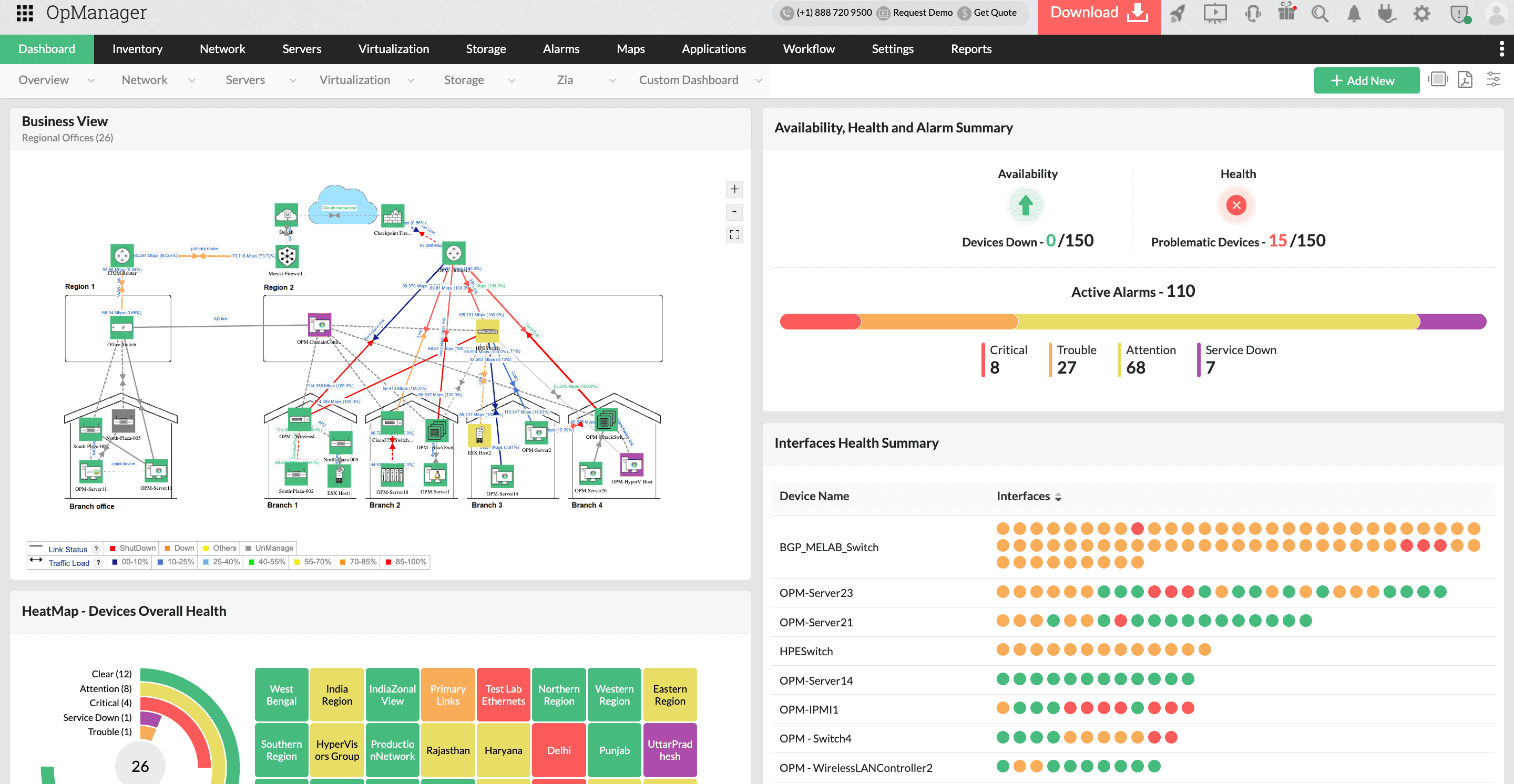
ManageEngine OpManager
Network Monitoring
Learn more about ManageEngine OpManager
POWR
No-Code
Learn more about POWR
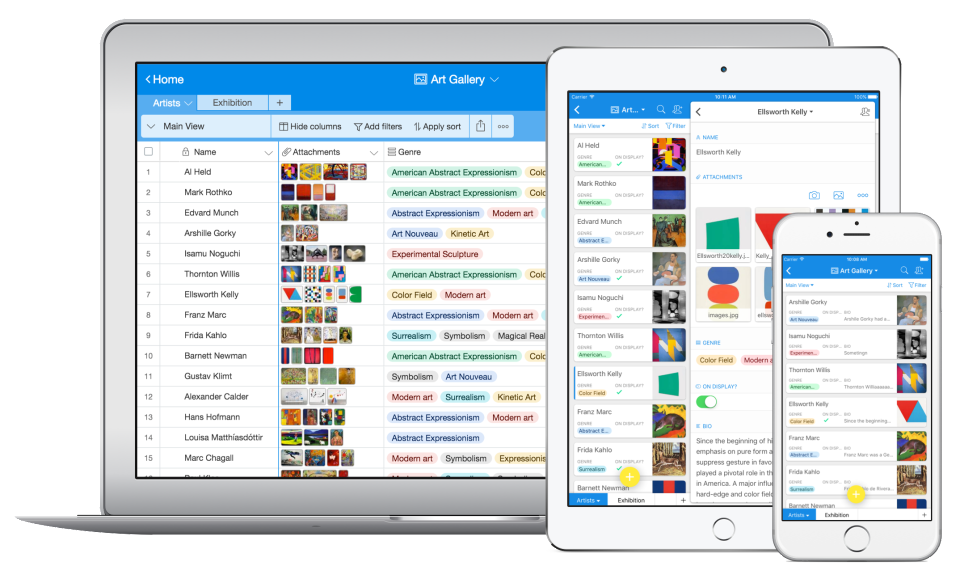
Airtable
No-Code
Learn more about Airtable

Pandora FMS
IT Monitoring
Learn more about Pandora FMS
Wisper 360
IT Asset Management
Learn more about Wisper 360

Mailinblack
Cybersecurity
Learn more about Mailinblack
IKare
Cybersecurity
Learn more about IKare
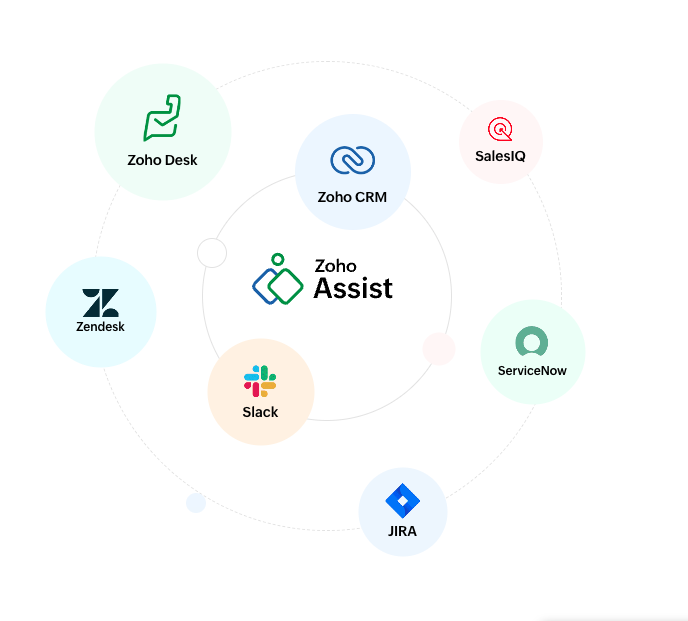
Zoho Assist
Remote Access
Learn more about Zoho Assist
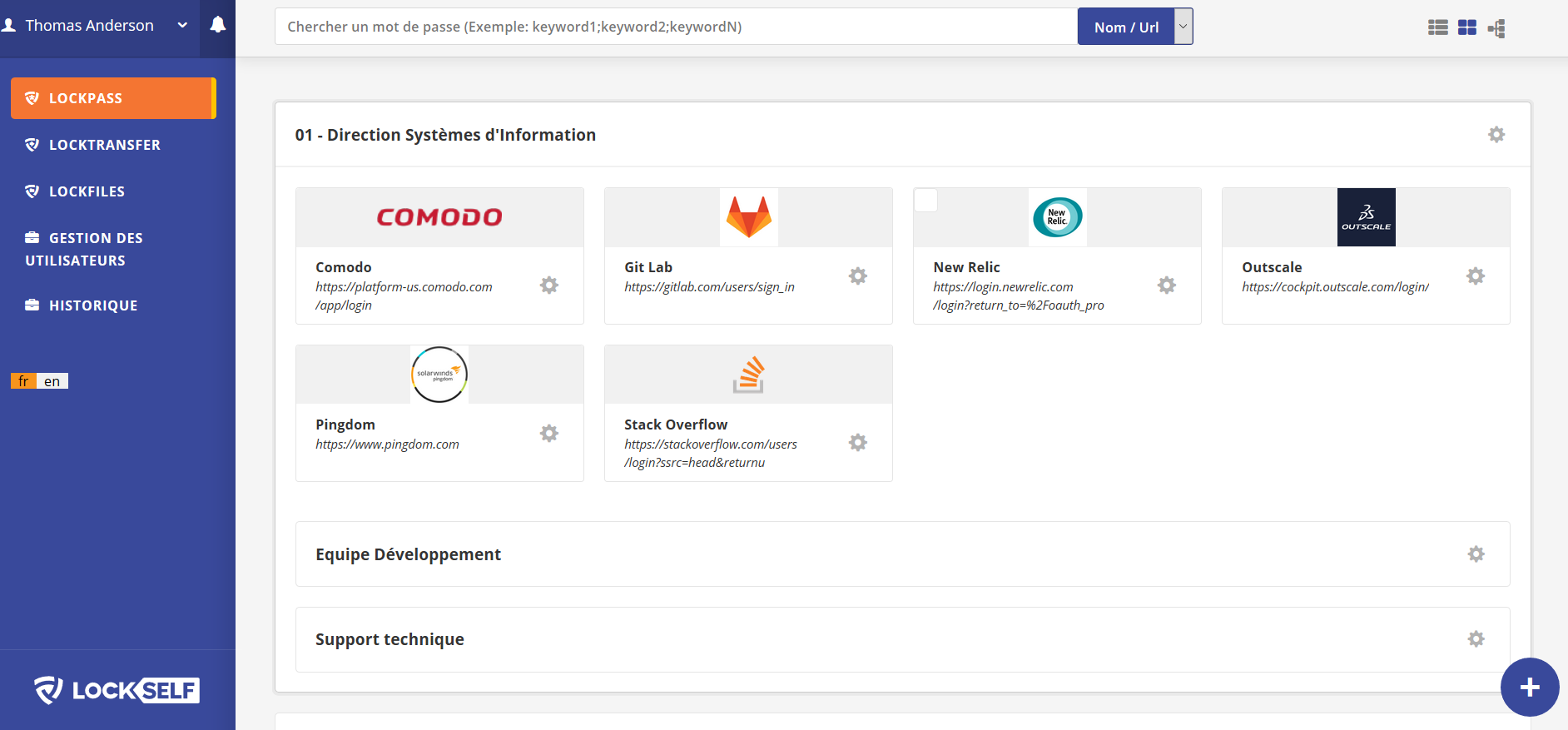
LockPass
Identity & Access Management
Learn more about LockPass
Site24x7
Website Monitoring
Learn more about Site24x7

Software • August 12, 2025
Gemini vs ChatGPT: which generative AI to choose to boost your productivity in 2025?
Full comparison Gemini 1.5 vs ChatGPT-5: features, pricing, integrations, use cases... Find out which generative AI best meets your business needs in 2025.

Definition • August 11, 2025
Using artificial intelligence in business: 25 examples and software to inspire you!
How can you make the most of artificial intelligence to get your business off the ground? There are many use cases, and here are 25 convincing examples to inspire you.

Software • August 11, 2025
Improve your efficiency without breaking the bank with these 15 free AI programs
Discover 15 free artificial intelligence software applications to automate your tasks, create content, analyze your data or code faster.

Software • August 8, 2025
These 20 AI apps that will change the way you work
Explore the 20 best AI apps to use in 2025 to save time, create, automate and go faster every day.

Software • July 25, 2025
Protect your data with these 12 file backup programs
Disaster, computer attack... your business data is vulnerable and needs protecting. The solution? Backup software. To help you choose yours, we've put together a comparison of the best solutions on the market.

Software • July 17, 2025
Control is just a click away with our 13 best remote control software packages
Discover our comprehensive guide to the 13 best remote control software packages, combining security, ease of use and advanced features, tailored to the needs of modern businesses and IT professionals.

Software • July 17, 2025
What are the best alternatives to TeamViewer? 13 software products to discover
Explore the 13 best alternatives to TeamViewer, both free and paid, for remote office. From AnyDesk to Zoho Access, find the ideal tool for your connectivity needs. A must-read for optimizing your efficiency and remote connectivity!

Software • July 15, 2025
Looking for an alternative to Wayback Machine? Here are 10 tools for archiving a website in 2025

Tip • July 10, 2025
API management, a must for business growth
API management makes it possible to design, monitor and analyze a company's various APIs. Appvizer tells you everything you need to know about API management.

Software • July 10, 2025
Don't get lost in creating your organization charts with these 10 tools
Would you like to create an organization chart easily, but don't have any graphic design skills? Appvizer offers you its selection of the best software to create your flowchart easily.

Tip • July 4, 2025
Incident management process, to transform crises into opportunities for continuous improvement
Discover why and how to set up a standardized incident management procedure, and a selection of software to support you.

Software • July 4, 2025
The 6 best VPN software solutions to secure your business in 2025
Discover the best VPN software of 2025 to protect your online data, bypass geographic restrictions and surf securely. Full comparison of free and paid options.

Software • July 4, 2025
6 scanning programs to automate document capture
Compare 6 scanning software packages to automate document capture: Kofax Capture, Canon CaptureOn Touch Pro, IRISPowerscan 10, Bluemega, Continia, ITESOFT.

Software • July 4, 2025
The 15 best password managers in 2025 for securing business access
Which is the best password manager 2025? Discover the features and benefits of each solution, and ensure your company's security.
IT tools facilitate project management, collaborative work and data security. From online workspaces to automatic backups, you can provide an efficient work environment for all of your employees. Stay informed about the latest online software innovations through our software guide!